Cisco Zero Trust
Overview
Cisco Zero Trust offers a comprehensive solution to secure all access across your applications and environment, from any user, device, and location. This complete zero trust security model allows you to mitigate, detect, and respond to risks across your environment. See how you can make your environment Cisco Secure today.
Cisco Zero Trust Overview
Why Cisco Zero Trust?
The most successful zero-trust solutions should seamlessly integrate with your infrastructure without entirely replacing existing investments. Cisco Zero Trust provides a comprehensive approach to securing all access across your applications and environment, from any user, device, and location.
Definition
Zero trust is a strategic approach to security that centers on the concept of eliminating trust from an organization's network architecture. Trust is neither binary nor permanent. We can no longer assume that internal entities are trustworthy, that they can be directly managed to reduce security risk, or that checking them one time is enough. The zero-trust model of security prompts you to question your assumptions of trust at every access attempt.
Cisco believes a zero trust security strategy is best executed by taking a connected, cohesive, and holistic approach.
A zero-trust approach:
- Establishes trust in every access request, no matter where it comes from
- Secures access across your applications and network
- Extends trust to support a modern enterprise across the distributed network
How is a zero-trust approach different?
Traditional security approaches assume that anything inside the corporate network can be trusted. The reality is that this assumption no longer holds true, thanks to mobility, BYOD (bring your own device), IoT, cloud adoption, increased collaboration, and a focus on business resiliency. A zero-trust model considers all resources to be external and continuously verifies trust before granting only the required access.
Principles
The platform approach of Cisco Zero Trust provides a balance between security and usability. Security teams can make it harder for attackers to collect user credentials and network access and to move laterally, and users can get a consistent and more productive security experience--regardless of where they are located, what endpoints they are using, or whether their applications are on-premises or in the cloud. Its comprehensive approach to securing all access protects the workforce, workloads, and workplace.
- Establishing trust
- Enforcing trust-based access
- Verifying trust continuously
We establish trust by verifying:
- User and device identity
- Device posture and vulnerabilities
- Any workloads
- Application and service trust
- Any indicators of compromise
We enforce least privilege access to:
- Applications
- Network resources
- Workload communications
- All workload users and administrators
We continuously verify:
- That original tenets used to establish trust are still true
- That traffic is not threat traffic
- Any risky, anomalous, and malicious behavior
- That the trust level is changed, if compromised
Architecture
Cisco Secure Reference Architecture
Cisco Zero Trust Framework
Zero-trust pillars
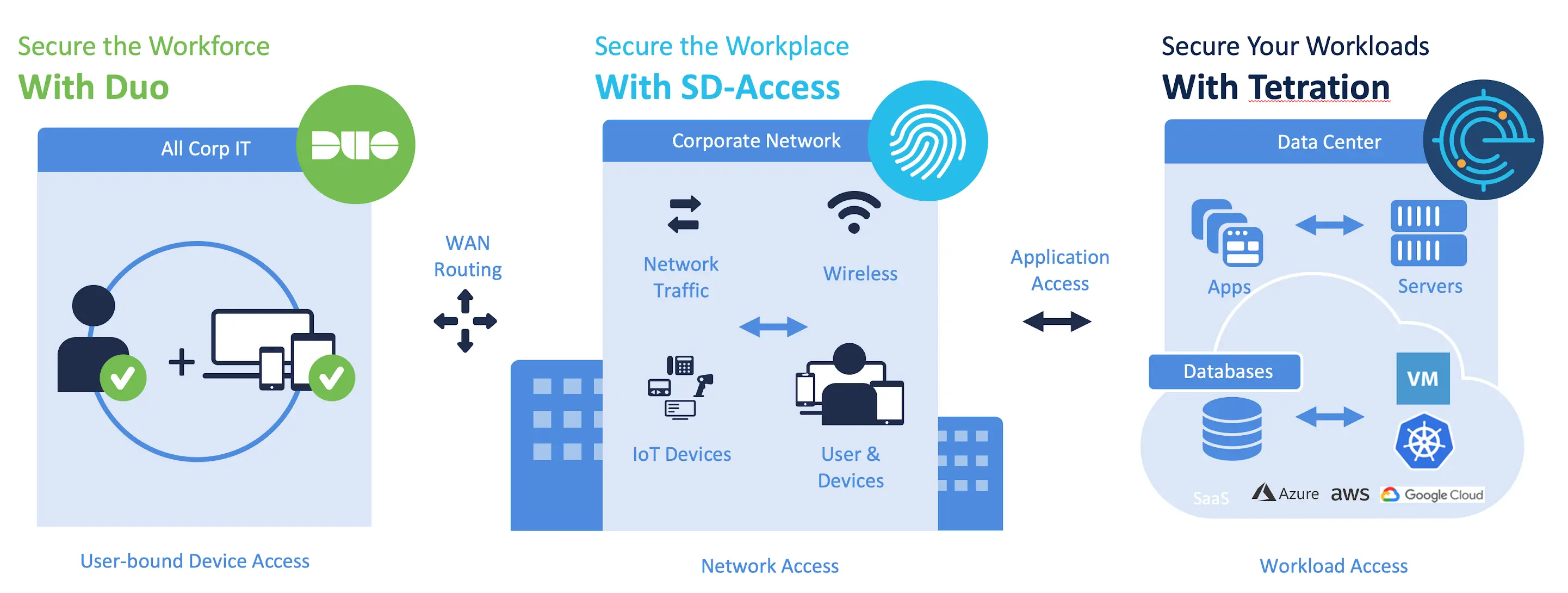
Security is not one-size-fits-all. When approaching zero-trust design, it is easier to break it down into three pillars: workforce, workload, and workplace. These align with the model proposed by Forrester to simplify adoption. There are nuances to address in each area, while all work toward the same goal.
- Zero trust for the workforce
- Zero trust for workloads
- Zero trust for workplace
This pillar focuses on making sure users and devices can be trusted as they access systems, regardless of location. Cisco Zero Trust provides solutions that establish trust in users and devices through authentication and continuous monitoring of each access attempt, with custom security policies that protect every application. It allows you to:
- Protect against credential compromise - Verify your users' identities with multi-factor authentication.
- Gain visibility into access activities - Get visibility into access activity across all locations, devices, and users. Control cloud application access and prevent malicious connections.
- Enforce access policies for every application - Set policies based on your organization's risk tolerance level and requirements.
- Protect against email compromise - Detect fraudulent senders while adapting in real time to block phishing attacks and malware.
- Enforce trustworthiness of user devices - Identify risky devices, enforce contextual access policies, and report on device health using an agentless approach or by integrating with your device management tools.
- Block access from compromised devices - Protect endpoints, network, and email and get visibility into network and endpoint threats while blocking and removing malware.
This pillar focuses preventing unauthorized access within application environments irrespective of where they are hosted. Cisco Zero Trust secures connections for all APIs, microservices, and containers that access your applications, whether in the cloud, data center, or other virtualized environment. Cisco Zero Trust, deployed on-premises or in the cloud, secures your app stack, and micro-segmentation helps you contain threats and protect against lateral movement.
- Visibility into applications - Have control over every connection from users and devices to both your applications and your network, across a multicloud environment.
- Application segmentation - Minimize lateral movement for on-premises and multicloud environments.
- Monitor application performance - Identify root causes of threats with deep diagnostic capabilities.
- Enforce policies and controls - Enforce application-specific user and device access policies to meet your organization's security requirements for access. Flag anomalies using behavioral analysis to reduce your attack surface.
- Gain clarity into application architecture - Visualize every component and dependency, across any environment, with flow maps.
- Remediate threats quickly - Contain threats by quarantining any servers with anomalous processing behavior.
This pillar focuses on secure access to the network and for any and all devices (including IoT) that connect to enterprise networks. Cisco Zero Trust enables users to securely connect to your network from any device, anywhere while restricting access from non-compliant devices. Our automated network-segmentation capabilities let you set micro-perimeters for users, devices, and application traffic without requiring network redesign.
- Secure network access - Get complete visibility by identifying, classifying, and assembling the necessary context on users and endpoints, including IoT.
- Network segmentation - Build granular segmentation directly into the network, eliminating the need for complicated infrastructure configurations.
- Encrypted traffic analytics - Identify malware in encrypted traffic using network analytics.
- Dynamic visibility - Build visibility-based network segmentation and policy control into your security architecture.
- Automated threat containment - Implement adaptive threat containment to ensure the organization's security posture evolves as threats do.
- Policy enforcement - Ensure policy is enforced close to source on unencrypted traffic, as well as in the network, based on encrypted traffic analytics.
Sharing signals across Cisco Zero Trust Architecture
Top Resources
- Zero Trust: Workforce solution design guide
- Workforce: Zero-trust evaluation guide for the workforce
- Cisco Zero Trust Workshops
- Zero Trust: Going Beyond the Perimeter
- Cisco Zero Trust: Mapped to Forrester's ZTX