Zero Trust Knowledge Base (ZTKB)
Purpose
- Organized and up to date list of the best zero trust resources
- Demystify Zero Trust Marketing from reality
- Have Suggestions? Let us Know!
If you work in product marketing, this knowledge base might contradict your asinine marketing ploys!
Zero Trust Definition
NIST's definition of Zero Trust:
Some History of Zero Trust
2004
An international group of corporate CISOs and vendors known as the Jericho Forum focuses on solving the "de-perimeterization" problem. They call for "the need for trust."
Jericho Forum's Identity Commandments
2009
Forrester coins the term "Zero Trust"
2014
Google release BeyondCorp, the first Zero Trust architecture
2017
Forrester releases Zero Trust eXtended
2020
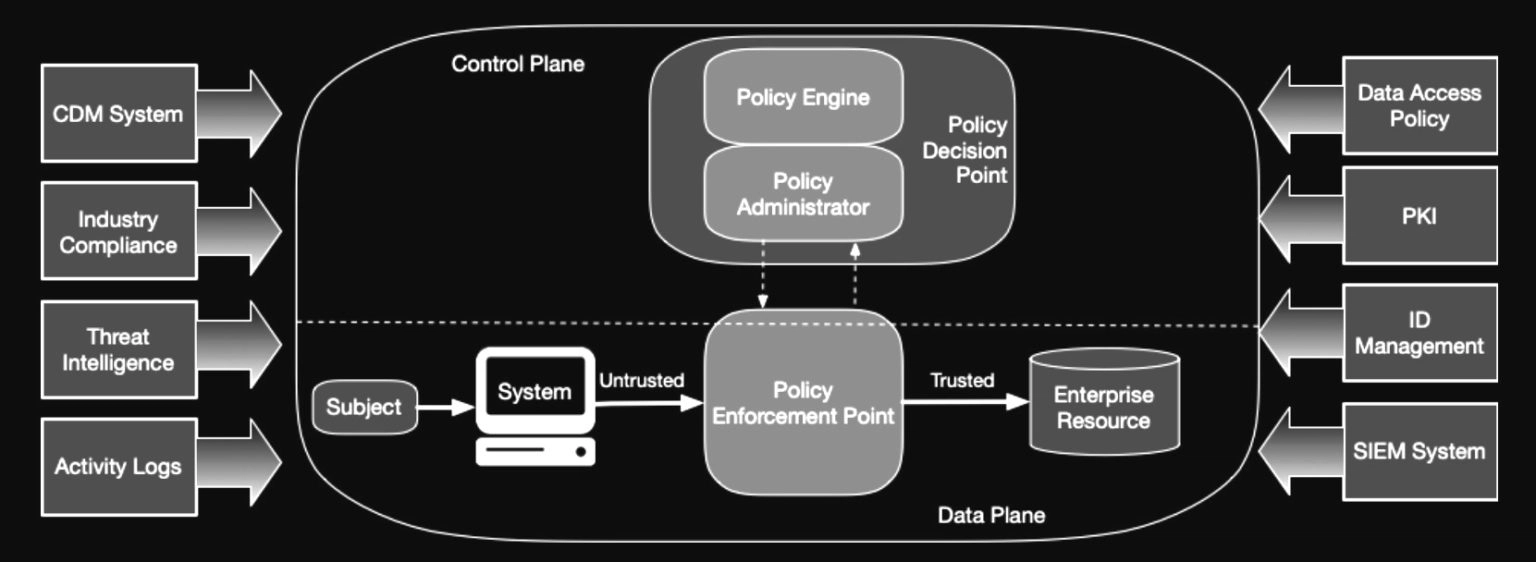
NIST releases 800-207 Zero Trust Architecture
"The concept of zero trust has been present in cybersecurity since before the term “zero trust” was coined." NIST SP 800-207
Zero Trust vs Traditional Perimeter Based Defense
- Traditional Security
- Zero Trust Security

-
In traditional, perimeter based defense, trust is based on the network location that an access request is coming from.
-
Once attackers are in the network, they can move laterally with a network get to get to an organization's 'crown jewels' - that is, its most valuable data.
-
The traditional model is antiquated. It does not extend security to the new perimeter of cloud, mobile, and hybrid environments.
-
In the Zero Trust approach, trust is established for every access request, regardless of where the request is coming from.
-
Zero Trust secures access across your applications and network. It ensures only the right users and devices have access.
-
Zero Trust extends trust to support a modern enterprise with BYOD, cloud apps, hybrid environments, and more.
Zero Trust Outcomes